Idp OAuth 2.0 code flow setup
Overview
OAuth 2.0 is an authorization framework that enables third-party applications to obtain limited access to an HTTP service, either on behalf of a resource owner or by allowing the third-party application to obtain access on its own behalf. OAuth 2.0 provides authorization flows for web and mobile applications to securely access resources on behalf of a user.
Akkess IAM supports OAuth 2.0 authorization code flow for issuing IAM token. To enable OAuth 2.0 authorization code flow, you need to configure the OAuth 2.0 client in the Idp and provide the client details in the Akkess IAM Idp configuration. Properties like
client_idclient_secretauthorization_urltoken_urluserinfo_urlsubject attribute mapping
are needed to be configured in the Akkess IAM Idp configuration.
To simplify the IAM console has templates for common Idp's OAuth 2.0 code flow setup.
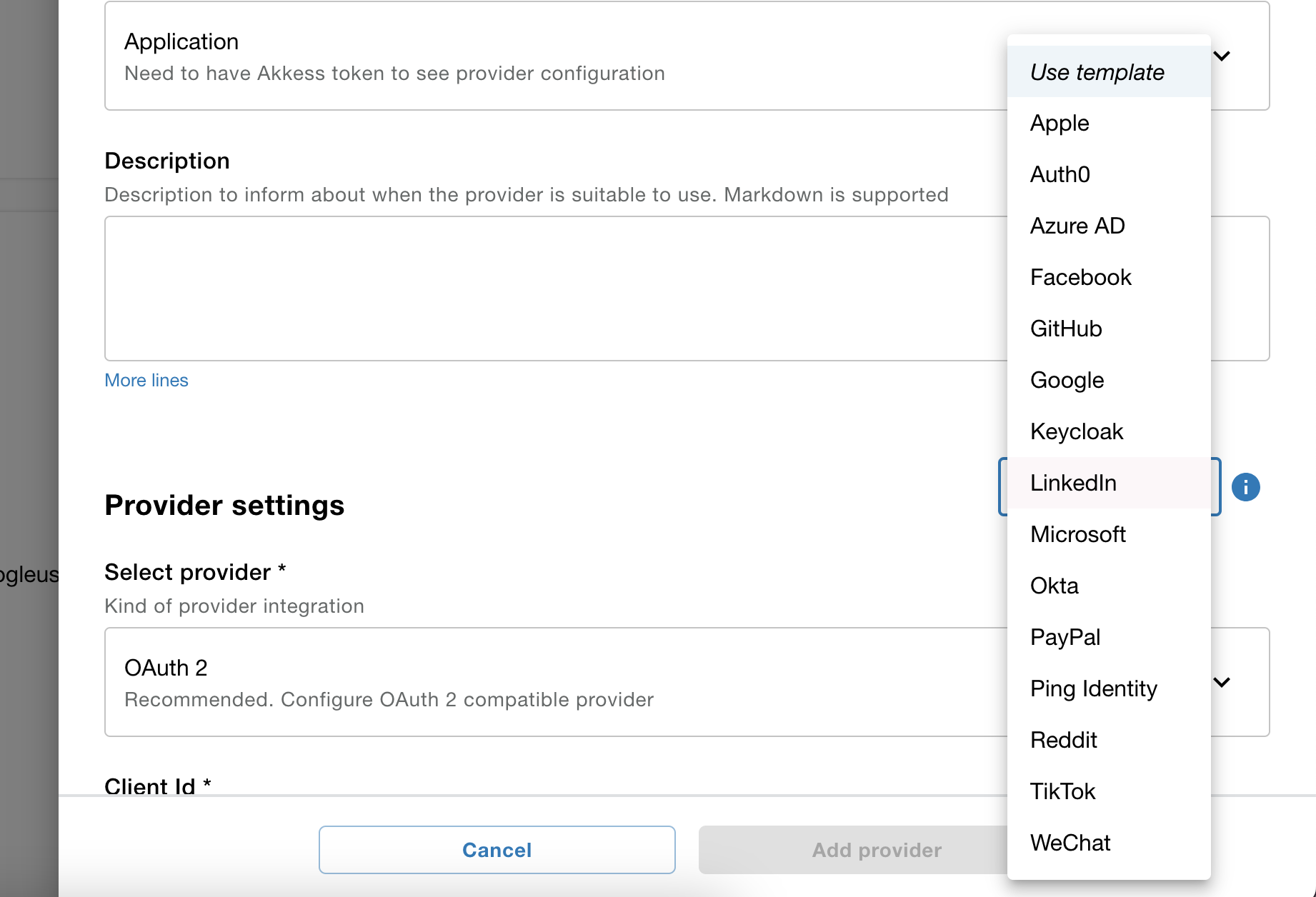
Common Idp's OAuth 2.0 code flow setup
Google
Step 1: Create a Google Cloud Project
- Go to the Google Cloud Console.
- Click Create Project, provide a name, and click Create.
- Select your project from the dropdown in the navigation bar.
Step 2: Enable APIs and Services
- Navigate to APIs & Services > Library.
- Enable the Google People API.
Step 3: Configure OAuth Consent Screen
- Go to APIs & Services > OAuth Consent Screen.
- Fill in required fields:
- App Name
- Support Email
- Developer Contact Information
- Save and proceed.
Step 4: Create OAuth Credentials
- Navigate to APIs & Services > Credentials.
- Click Create Credentials > OAuth 2.0 Client IDs.
- Add the Redirect URI and save the Client ID and Client Secret.
Facebook
Step 1: Create a Facebook App
- Go to the Facebook Developers Portal.
- Click Create App, choose Consumer, and provide a name.
- Complete the app setup.
Step 2: Configure OAuth
- Navigate to Settings > Basic.
- Add your Redirect URI under OAuth Redirect URIs.
- Save the App ID and App Secret.
Step 3: Implement OAuth in Your App
- Use the App ID and App Secret to handle the OAuth flow securely.
GitHub
Step 1: Register Your Application
- Go to GitHub Developer Settings.
- Click New OAuth App and provide details:
- Application Name
- Homepage URL
- Authorization Callback URL
Step 2: Note Your Credentials
- Save the Client ID and Client Secret.
Step 3: Use OAuth in Your App
- Use these credentials to manage the OAuth 2.0 flow in your app.
Microsoft
Step 1: Register an App in Azure AD
- Go to the Azure Portal.
- Navigate to Azure Active Directory > App Registrations > New Registration.
- Provide a name and Redirect URI.
Step 2: Configure API Permissions
- Add permissions for
openid,email, andprofile. - Grant admin consent if required.
Step 3: Note Your Credentials
- Save the Application (client) ID and Directory (tenant) ID.
- Generate a Client Secret.
Step 4: Implement OAuth
- Use these credentials to initiate OAuth 2.0 in your app.
Apple
Step 1: Register a Service ID
- Log in to the Apple Developer Console.
- Go to Certificates, Identifiers & Profiles > Identifiers > Service IDs.
- Create a new Service ID and enable Sign In with Apple.
Step 2: Configure the Redirect URI
- Add your Redirect URI to the Service ID configuration.
- Save your Client ID.
Step 3: Generate a Key for Authentication
- Go to Keys > Create a Key.
- Enable Sign In with Apple.
- Save the Key ID and download the private key file.
LinkedIn
Step 1: Register Your App
- Log in to the LinkedIn Developer Portal.
- Click Create App, provide details, and submit.
Step 2: Configure OAuth
- Go to your app settings and add your Redirect URI.
- Save your Client ID and Client Secret.
Step 3: Enable Permissions
- Enable scopes such as
r_liteprofileandr_emailaddress.
Step 4: Use OAuth in Your App
- Use your Client ID and Client Secret to handle OAuth 2.0 securely.
TikTok
Step 1: Register Your App
- Go to the TikTok Developer Portal.
- Sign in and click My Apps.
- Click Create App and provide the necessary details (name, description, etc.).
Step 2: Configure OAuth Settings
- Navigate to App Settings.
- Add your Redirect URI (e.g.,
https://yourapp.com/oauth2callback). - Save the changes and note your Client Key and Client Secret.
Step 3: Implement OAuth in Your App
- Use the Client Key and Client Secret to initiate the Authorization Code Flow.
- Ensure your app handles the redirect URI securely.
PayPal
Step 1: Create a PayPal App
- Log in to the PayPal Developer Dashboard.
- Navigate to My Apps & Credentials.
- Click Create App, name it, and select the sandbox/live environment.
Step 2: Configure OAuth
- Note the Client ID and Secret for your app.
- Add your Redirect URI under the App Settings.
Step 3: Enable Scopes
- Ensure that necessary scopes like
openid,profile, andemailare enabled.
Step 4: Use OAuth in Your App
- Use the credentials to handle the OAuth 2.0 flow in your app securely.
WeChat
Step 1: Register on the WeChat Open Platform
- Go to the WeChat Open Platform.
- Sign in and create an application.
Step 2: Configure OAuth
- Add your Redirect URI under Authorized Callback Domain.
- Save and note your AppID and AppSecret.
Step 3: Implement OAuth
- Use the WeChat API with your credentials to initiate the flow.
Reddit
Step 1: Create a Reddit App
- Log in to the Reddit Developer Portal.
- Click Create App and provide details (name, description, etc.).
- Select Web App and add your Redirect URI.
Step 2: Configure OAuth
- Note your Client ID and Secret.
- Use the provided credentials to handle the OAuth flow.
Step 3: Implement OAuth in Your App
- Ensure your app securely handles redirect URIs and stores sensitive credentials.
Auth0
Step 1: Create an Auth0 Tenant
- Log in to the Auth0 Dashboard.
- Click Create Tenant and provide the necessary details.
Step 2: Configure Applications
- Navigate to Applications > Create Application.
- Choose Regular Web Application.
- Add your Redirect URI in the application settings.
Step 3: Use OAuth in Your App
- Note the Client ID and Client Secret.
- Ensure your backend securely handles sensitive credentials and redirect URIs.
Okta
Step 1: Create an Okta Developer Account
- Go to the Okta Developer Console.
- Sign up or log in to your account.
Step 2: Configure OAuth Settings
- Create a new app in Applications > Add Application.
- Select Web and configure your app.
- Add your Redirect URI in the app settings.
Step 3: Note Your Credentials
- Save your Client ID and Client Secret for the app.
Step 4: Implement OAuth
- Use the credentials in your application to manage OAuth 2.0 flow securely.
Keycloak
Step 1: Set Up Keycloak
- Access your Keycloak Admin Console.
- Create a Realm or select an existing one.
Step 2: Register a Client
- Go to Clients > Create.
- Provide a Client ID and configure the client.
- Add your Redirect URI in the client settings.
Step 3: Secure OAuth Flow
- Note the Client ID and Client Secret.
- Configure your application to handle the Authorization Code Flow securely.
Azure AD
Step 1: Register Your Application
- Log in to the Azure Portal.
- Go to Azure Active Directory > App Registrations > New Registration.
- Provide a name and add your Redirect URI.
Step 2: Configure API Permissions
- Add necessary API permissions (e.g.,
openid,email,profile). - Grant admin consent if required.
Step 3: Note Your Credentials
- Save the Application (client) ID and Directory (tenant) ID.
- Generate a Client Secret.
Step 4: Implement OAuth
- Use the credentials to initiate and manage OAuth 2.0 flows in your app.
Ping Identity
Step 1: Access Ping Identity Admin Console
- Log in to your Ping Identity Admin Console.
- Create or select an existing Application.
Step 2: Configure OAuth
- Add your Redirect URI to the application configuration.
- Save the Client ID and Client Secret.
Step 3: Implement OAuth
- Use the credentials in your app to securely manage OAuth 2.0 flow.
References
- Each IdP's developer documentation is recommended for detailed setup instructions and specific configurations.