Effortless API security
Integrate robust API authentication in a breeze, featuring seamless role and permission management.
Authentication
Integrate with well known Identity providers for both custom setup and social login. You can also use your own OAuth2 or OIDC compliant solution.
Authorization
Authorize your users on both feature and data level. Akkess supports with best practices to implement reliable and fast access management on data level.
Akkess Token
The Akkess Token keeps a customized set of attributes and is used for authorize client requests and apply fine-grained access control.
Access Management
Full customization of roles and permissions. You decide who can do what.
Roles
Manage your roles and their permissions in one place. Changes can be applied in runtime.
Permission
Services define their own permissions with built-in support for declaring fine-grained access control capabilities.
Organization
Built-in support for defining your structure. Organize your branches, company or social app.
Users
Enroll your users using email, invite codes or self-registration. Multiple identities are supported.
Systems and devices
Services and devices are first-class citizens in Akkess. These can interact in same way as any end user can.
Cloud agnostic
Akkess is delivered via docker containers and can be deployed on any cloud provider, on-premise or locally. You are in control.
Integrity
Protect your domain model from unintended and unauthorized changes with the use of backend-for-frontend services and our application firewall.
Tenants
Each tenant is its own isolated island and cannot share data with other tenants within Akkess.
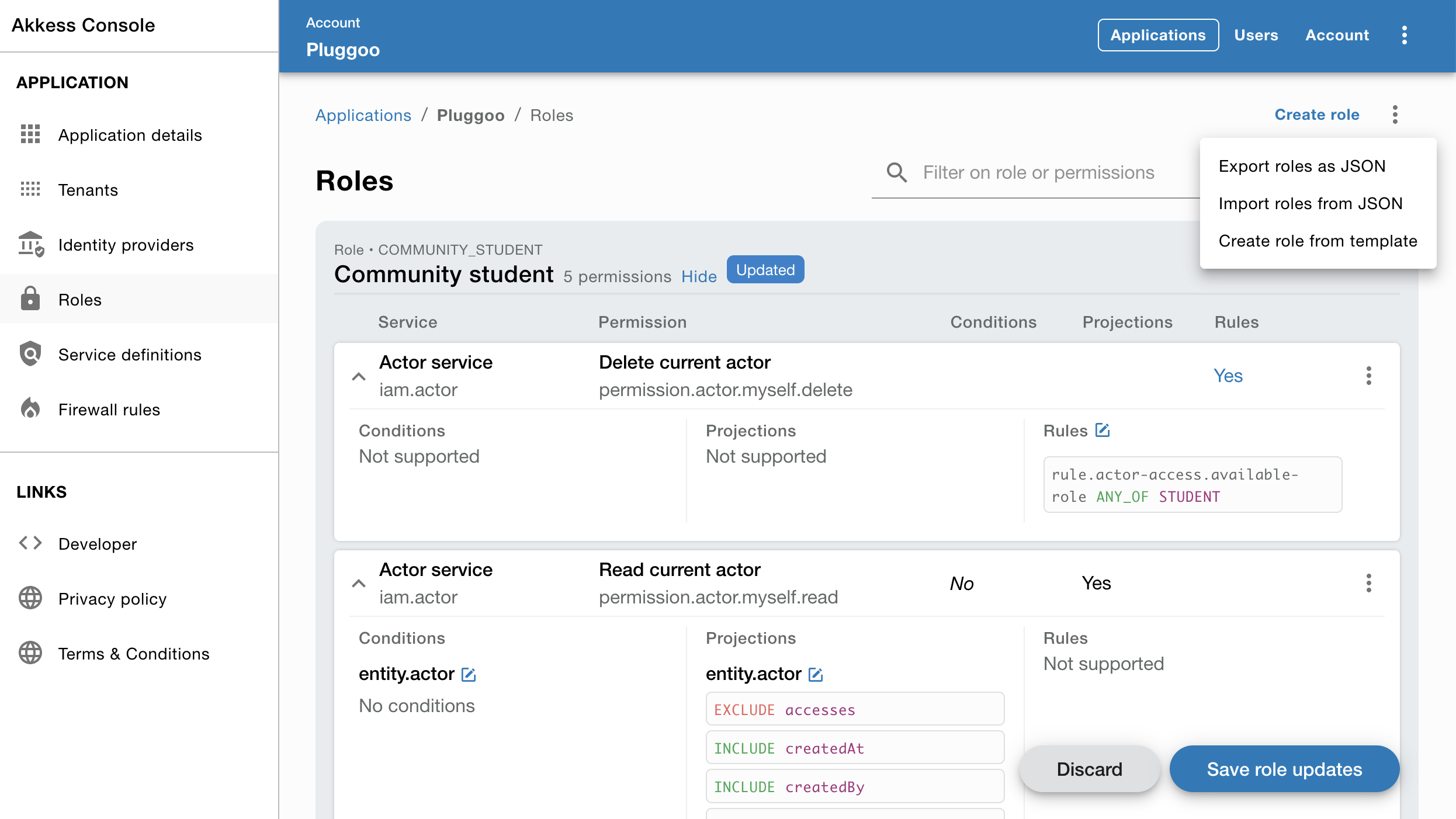
IAM Console
Akkess IAM Console is used for managing the Akkess IAM service and can also be used as a support tool for managing data within a single tenant in your application.
Some features:
- Setting up account, applications and tenants
- Configure roles and permissions
- Firewall configurations
- IdP integration setup
- Manage actors
- Manage nodes

Easy to Use
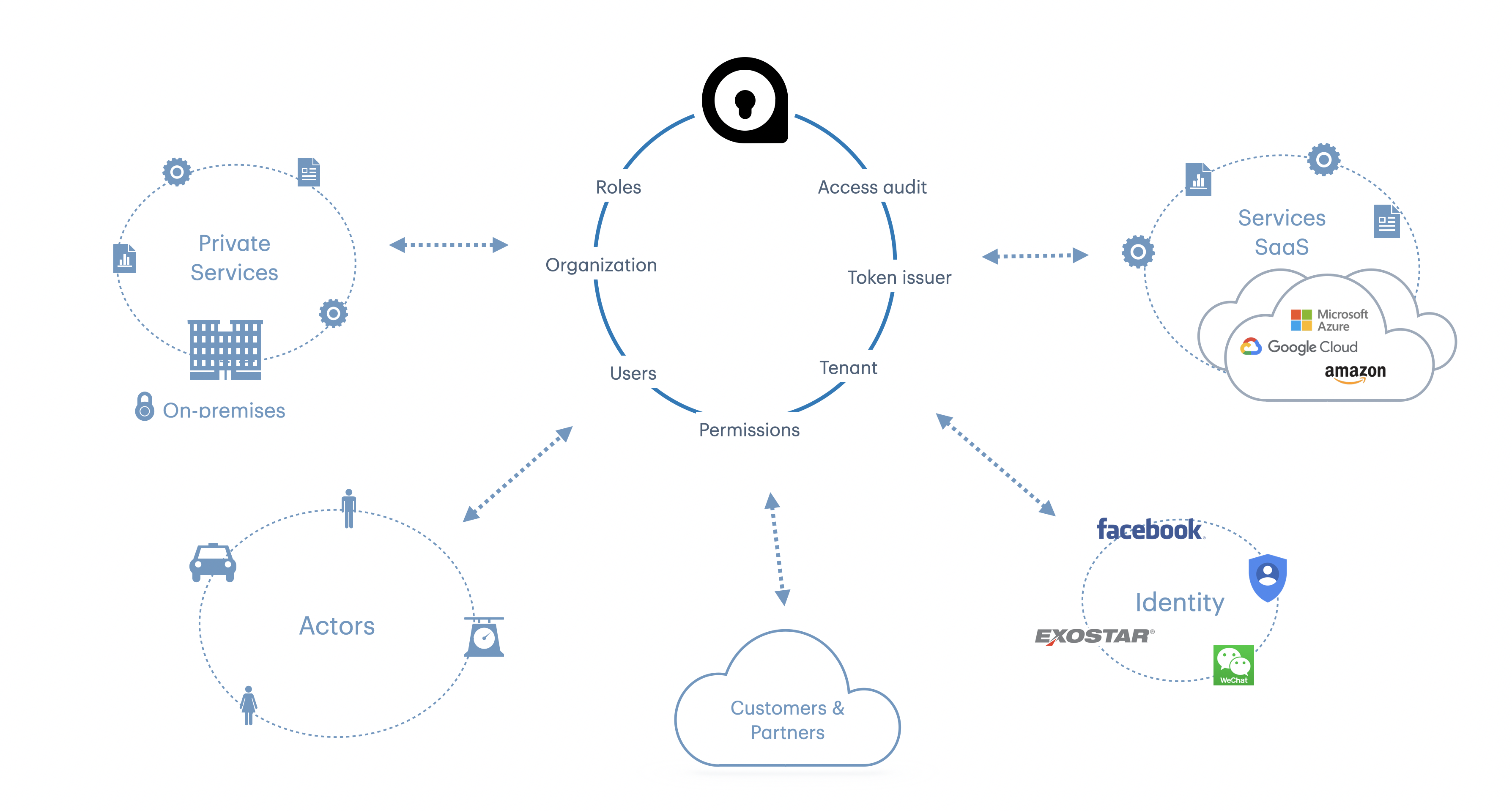
Akkess IAM is a toolbox to enable secure and reliable hierarchical access management for any kind of application.Domain driven
Roles, permissions, groups and organizations are configurable to reflect your domain and your nomenclature.Authorization
Authorize your users on both feature and data level. Akkess supports with best practices to implement reliable and fast access management on data level.Powered by robust tools
From local development to production, Akkess IAM is designed to be deployed on any container compatible environment.API driven
Integrate, manage and automate your access management with Akkess IAM API using our SDK or our OpenAPI specifications.Authentication
Works with your preferred identity stack, Akkess IAM is designed to be integrated with any OAuth2 or OIDC compliant IDP.A modern IAM stack balances user experience, privacy, and security
Cut complexity, boost productivity
Streamline security and growth, from setup to scale with Akkess IAM solution
Accelerate
Akkess IAM is a solution for implementing fine-grained access control on application level into your system.
It is built for developers and follows industry standards for implementing access control. Using Akkess IAM you will get up to speed quickly with access management and be able to focus on your core business flows instead of developing own authentication and access system.
Akkess IAM is a toolbox where you can choose the pieces that fits your project. Start small and grow with your needs!
Access control
Create roles and assign permissions to your roles. The roles are used apply fine-grained access control in the system for all end users. Additionally, more complex data sharing and access control rules can be applied by combining this with a hierarchy of nodes.
For example, a car owner might have role CAR_OWNER and the car might have role CAR and could be configured like:
CAR_OWNERhas permission to readcar positionsfor the car it ownsCARhas permission to write its owncar positionFLEET_MANAGERhas permission to read allcar positionsfor all cars in associated toFLEETnode
The roles and their respective resource association are provided in the IAM token which in turn makes it possible for the car-position service to accept or reject calls without the need of calling any external or internal service.
By only relying on the information provided by the IAM token makes the service fast, efficient and autonomous.
Model your domain
Use the concepts of actors and nodes to model your domain. Define your types of actors and nodes your application has and how they are related.
Actors are typically the end users in your system and nodes are the resources they can access. Apply a hierarchy of nodes and actors to define access control and relations.
For example, role DEPARTMENT_MANAGER has manage access to all child nodes of an associated DEPARTMENT node, while role WORKER only has read access to the DEPARTMENT node that it belongs to.
Associate identity providers
The end user's identities are kept out-side of Akkess and are managed by your identity provider (IdP). This pattern makes your application IdP agnostic and enable that you can add additional IdPs later without it affecting your services.
Configure your trusted IdP in Akkess and let the IdP take responsibility of authenticating end users. When authenticated by the IdP, the IdP token is used to issue an IAM token. Akkess checks your trusted IdP configuration and verify the IdP token before returning a signed IAM token.
The IAM token is then used to the following calls in your system and Akkess services. The IAM token contains relevant information about the actor and its access so your service don't need to have any knowledge about the IdP.
Develop
A service developer defines the permissions that their service support. For example car-position.read and
car-position.write. These permissions are registered in our service directory which in turn makes it possible to choose these permissions when
setting up a role for an application.
As a service developer you need to learn about the Akkess Token and how to use it to secure your services and applications.
The core parts are covered by the following questions:
- Who is the caller and which tenant does it belong to?
- How do I verify the token?
- How do I look up the permissions allowed?
That's it - as a service developer you don't need to know much more. Still you have all information to be able to secure
your services and store data and tag it with a tenantId and actorId that is globally unique and anonymized.
Deploy
Akkess IAM is packaged for running in your environment, and you will have full control over the data stored. The components are infrastructure agnostic and can be run on any cloud provider or on-premise. This makes it possible to make use of Akkess in your existing infrastructure and also to be compliant with your policies and any regulations in your domain.
Integrate
Let customers and partners take part of your services and data or enable third party services in your application. Simply add applicable roles and enroll the end users into your application and associate applicable nodes. This ensures that they will only have access to the data and services that they are allowed to use.
Third party services can be integrated into your application by using our service catalog.
Learn more
See our documentation for additional details and visit the IAM Console to get started.